Microsoft Entra Identity Governance Fundamentals: Access Packages
- Sebastian F. Markdanner
- Dec 9, 2024
- 12 min read
Updated: Jan 7
In this blog post, we’ll be covering the fundamentals of Access Packages in Microsoft Entra—it’s all about getting a solid understanding of the basics to help you get started on the identity governance road!

Managing privileged access users is made easier with Privileged Identity Management (PIM), but what about non-privileged users? How do we efficiently manage their access across our organization?
This is where Access Packages come in! They help you handle onboarding, offboarding, internal role changes, external contractors on specific projects, or even requests made on behalf of other users. Let’s dive in!
Table of Content
Understanding Microsoft Entra Identity Governance Access Packages
Access Packages are collections of resources and roles organized into entitlement management catalogs. These enable streamlined identity governance, allowing users to seamlessly gain or lose access as roles change. For instance, transitioning a new IT Supporter, Digital Designer, or Sales Representative becomes far more efficient.
This reduces downtime for employees, minimizes IT admin overhead, and decreases the risk of human error. At a high level, creating an Access Package involves:
Naming the package and associating it with a catalog
Defining the resources and roles
Configuring request and lifecycle policies
Applying custom extensions
Managing post-creation configurations like separation of duties and assignment policies
Let’s explore these steps in more detail.
Access package creation steps
Basics
The first step in creating an Access Package is assigning it a meaningful name and description, along with specifying the entitlement management catalog it belongs to.
Catalogs help organize resources and Access Packages, enabling better delegation of management. For example:
Different managers can oversee separate catalogs without affecting Access Packages or resources in other catalogs.
This creates clear boundaries and allows for department-specific or project-specific access management.
Resources
This is where we can define the resources and roles that the access package will grant to users. You can include multiple resources and roles, combining different types for flexibility.
Currently supported resource types:
Groups and Teams
Applications
SharePoint sites
Microsoft Entra roles (Preview)
Additional configuration options include:
Assigning custom app roles.
Specifying group membership as an owner or member.
Request configurations
Here, you define who can request access, how they can request it, and the approval flow. Key settings include:
Scoping: Controls who is eligible to request access—internal users, guests, or external users from connected organizations.
Approval Flows: Enables single or multi-stage approval processes. Approvers can include managers, users, or groups.
On Behalf Of: Allows managers to request access for their team members.
Microsoft Entra Verified ID: Requires users to provide identity proof for access requests, in the form of Verified ID.
Requestor information
To justify access requests and assist with audits, you can require additional information from users. This includes:
Customizable questions - e.g. “What is your business justification for this access?”
Answers can be configured for short text, long text or multiple choice
Options for mandatory or optional responses.
This feature is invaluable for audits and lifecycle management, especially in approval-based configurations.
Lifecycle management
Lifecycle management ensures access is granted and revoked appropriately. It includes:
Expiration Policies: Set access to expire on a specific date, after a set number of hours or days, or to never expire.
Access Reviews: Automate access re-certifications, building on the previously discussed capabilities. This is especially useful when expiration periods are long.
Custom Extensions
Custom Extensions allow for advanced functionality by integrating Azure Logic Apps. These can:
Automate actions during request flows.
Execute custom processes before an assignment expires.
Create advanced custom requests, such as creating Temporary Access Pass on behalf of users
This is ideal for scenarios that require configurations beyond the native capabilities of Access Packages.
Post creation configuration: Duty Separation
After creating an Access Package, you can configure Separation of Duties policies to:
Prevent users from accessing conflicting roles or resources simultaneously.
View and enforce incompatibility rules between Access Packages or groups.
For example, in a developer environment, you might restrict access to multiple project-specific packages to ensure developers only work on their assigned projects, another use case could be for external users to ensure the users do not receive access they shouldn't have.
Post creation configuration: Assignment
You can define assignment policies to determine how users gain access:
Static Policies: Manually assign access.
Auto Policies: Automatically assign or remove access using Microsoft Entra ID Dynamic Group syntax. For instance:
Use user.memberOf to dynamically query and assign users based on group memberships.
Each Access Package can have multiple static assignment policies but only one auto-assignment policy.
A catalog can hold multiple Access Packages, each with unique assignment policies for internal and external users. The Access Package Manager role allows designated users to manage the packages in a catalog, even if they didn’t create them.
The diagram below illustrates how catalogs can include multiple Access Packages, each with its own unique assignment policies for internal and external users. This modular approach simplifies management while maintaining security.

Used with permission from Microsoft. Source: Microsoft Learn: What is entitlement management?
Access Package use cases
Now that we’ve covered the building blocks of Access Packages, let’s explore some scenarios where these capabilities truly shine. These examples highlight both the administrator’s perspective and the end-user experience and set the stage for the detailed step-by-step guides to follow.
Scenario 1: Automating Access for a Regional Sales Team
The EMEA sales team has recently hired a new representative, Gerhart Moller. Gerhart needs access to several key resources to perform his role effectively, including:
Microsoft Entra Groups for Marketing and Sales
The Salesforce application
A Microsoft 365 E5 license with Entra ID Governance features
Marketing resources stored in SharePoint
To streamline this process, access should be automatically assigned to users designated as EMEA sales personnel. Additionally, the setup must ensure that there’s no overlap with access for the AMER and APAC sales teams, preserving proper segregation of roles.
Scenario 2: Granting Project-Based Access to External Users
An ERP project has kicked off, requiring collaboration between contractors, vendors, partners, and the internal project team. These external collaborators need access to:
The resource tenant
Project-specific resources like a SharePoint site, a Teams channel, and a custom Entra role as an eligible assignment
Since the specific external users are not yet identified, the setup should allow for self-service sign-up from partnered tenants. External users must also provide a short description of their project role as part of the request. To maintain security, access should:
Be approval-based
Have a time-restricted duration
Undergo quarterly re-certifications
Scenario 3: Delegating Access Package Administration
Management has requested a more decentralized approach to administrative tasks, allowing middle management to oversee access for their department’s resources. This delegation would free up the IT team’s time and improve operational efficiency.
Each department should have:
Its own entitlement management catalog of resources and access packages
Designated delegates for creating and managing access packages
A catalog owner to oversee the governance grouping for their department
By implementing these roles, departments can take ownership of their access needs while ensuring compliance with governance policies.
These tailored scenarios set the foundation for the detailed configuration guides ahead, providing clear real-world contexts for implementing Access Packages effectively.
Configuring Entitlement Management for the various scenarios
Now that we’ve outlined the scenarios, it’s time to roll up our sleeves and configure the solutions. Let’s dive in step by step while keeping it straightforward and effective.
Scenario 1: Automating Access for a Regional Sales Team
Configuration
Access the Microsoft Entra portal, and via the Identity Governance menu, choose Entitlement Management and finally move into the Access packages menu.
Once here, choose New access package to start the new package.

Enter basic information
Provide a Name and Description for the access package
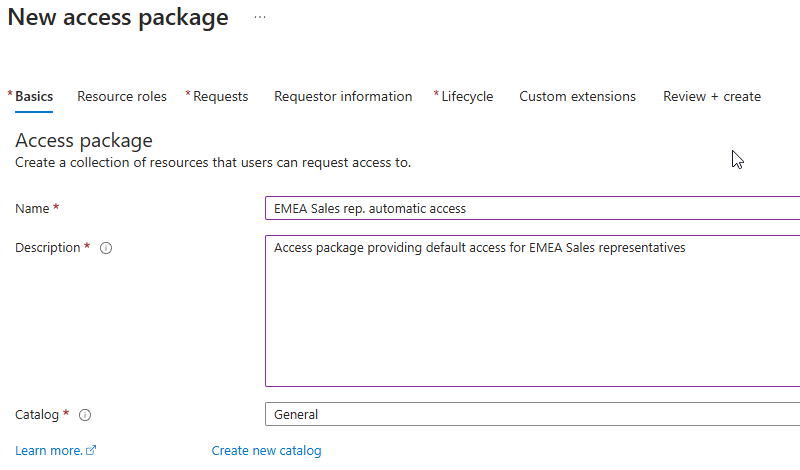
Enable See all [Group and Team(s)] not in the ['General'] catalog setting to choose the required resources. Add:
Sales and Marketing Team
Salesforce App
Microsoft E5 + ID Governance License group
Global Marketing Sharepoint site

Configure roles for each resource. Assign built-in or custom roles as needed, such as App Roles or specific group membership roles.
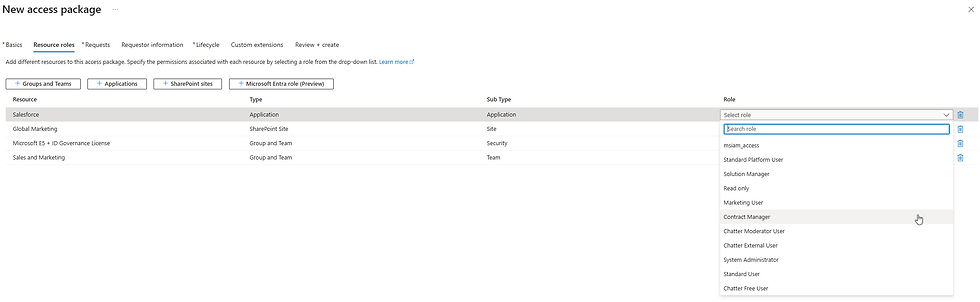

Define the initial request policy.
Set the request policy scope to None by setting Enable to No.
NOTE: While this initial policy won’t be used, it’s required for successful creation.

Skip Requestor information
Lifecycle Policy: Configure minimally as it won’t be used but is required for setup.

Skip Custom extensions
Review the configuration and create the access package.

Post-Creation configurations
After creating the access package, we must perform some post-creation configuration to meet the automatic assignment requirement in the task.
Open the newly created Access Package to view the overview.
Take note of the My Access portal link, as it will be used in a later scenario.

Access Policies to view the initial policy created during setup.
This policy includes the request policy, requestor information, access review, and custom extensions. It is currently disabled.
Select Add auto assignment policy

Configure the auto-assignment using Microsoft Entra Dynamic Groups syntax:
Enable Automatically create assignments.
Enable Automatically remove assignments.
Optionally, configure retention duration or add custom extensions.

Enter a name and description, review the setup, and create the policy.

Once the policy is created, you'll notice a new policy with the status of Always enabled.

Separation of Duties:
Add the required groups to enforce restrictions for users in the EMEA team.
This ensures users in other regional sales teams (AMER or APAC) cannot access the EMEA sales resources.

End-user experience
As this policy is automatically assigning the access, the user simply needs to logon for the access to update.
Before login:
A user in scope will be added to the auto-generated AutoAssignment group.

After login:
The user’s group memberships will update automatically, reflecting the resources configured in the Access Package.

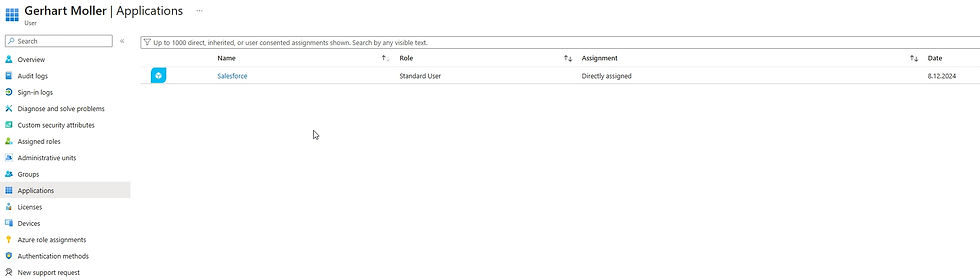

Using the My Access portal:
Users can log in to the portal and see the active Access Package assigned to them.

This configuration allows automatic assignment of resources for new and existing users, providing a seamless experience for all stakeholders.
Scenario 2: Granting Project-Based Access to External Users
Configuration: Connected organizations
Since this scenario provides external users with a self-service access option, even if they don't currently have access to the resource tenant, we must begin by connecting the organization(s) for which we want to enable this feature.
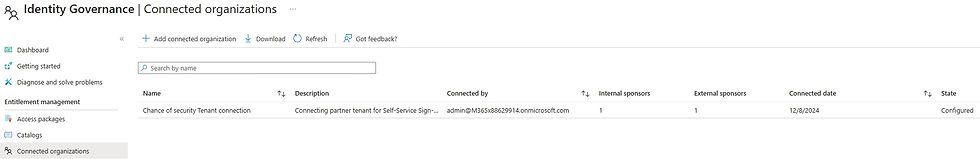
Navigate to Connected organizations in the Entitlement management blade.
Select Add connected organization

Provide details:
Enter a Name, Description, and set the state to Configured.
Only the Configured state enables self-service for external users.

Add external domains:
Under Directory + Domain, search for and add the domains of the external tenants (e.g., custom domains or .onmicrosoft.com).
Multiple domains can be added to simplify managing partner organizations, decreasing administrative overhead for project management.

Configure Sponsors
Assign Internal Sponsors (preferably multiple users or a group) and an External Sponsor (an existing guest user).


Review and create the connection

Once created, the connection will display its state and sponsor information
Configuration: Access Package
Follow the same steps as Scenario 1 to create the package but configure it specifically for external users.
To enhance project management, we'll create a new catalog for external users via the access package using the Create new catalog option.


Add the necessary project-specific resources.

Request Configuration:
For users not in your directory, choose the targeted organizations set up in the previous step or scope for all configured connected organizations.
Enable Approval Flow and configure approval stages as needed, utilizing the same capabilities as with access reviews.

Require external users to justify their role:
Ask users to provide a short description of their role during the request for auditing purposes.

Configure the Lifecycle Policy:
Set the expiration to On Date to ensure access is removed when the project ends.
Enable requests for shorter timelines with optional extensions.
Add quarterly Access Reviews, assigning managers as reviewers with fallback groups to review access.
Using manager will require configuring a manager for each external user.
Ensure if Reviewers don't respond is configured to Remove Access

Configure Custom extensions if needed.
Review and create the Access Package.

Post-Creation configuration: Expanding Access
Our initial policy is set up for external users, but the task requires enabling access for both internal and external users. To achieve this, we’ll need to create a secondary policy:
Inside the newly created access package, navigate to the Policies blade and choose Add Policy

Fill in the basic details for the new policy

Define who can request access:
Choose Users in your directory or None to set the scope for internal users.
If you choose “Users in your directory,” specify which users or groups are eligible for the policy.
Configure the approval flow:
Assign a specific approver. In this case, Christie, the project owner, has been designated as the primary approver.
Enable or disable the following settings based on the requirements:
Request on behalf of others: Allow managers or sponsors to make requests for their team.
Bypass approval: Skip the approval process if pre-approvals are in place.

Configure the Lifecycle policy:
Users cannot extend access and must request it anew.
Access review uses self-review for internal users, ensuring easier management and auditing re-certification.

After creating the internal user policy, multiple policies are active with the state Enabled set to Yes.

End-user experience - Internal user
Internal users can request access by signing into myaccess.microsoft.com and navigating to the Access Packages menu. Here’s how the process works:
The user selects the access package they need and clicks the Request button.
They can choose to:
Copy a direct link to the access package.
View the resources included in the package.
Continue to submit the request.

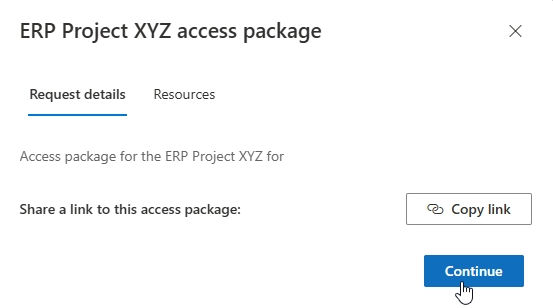
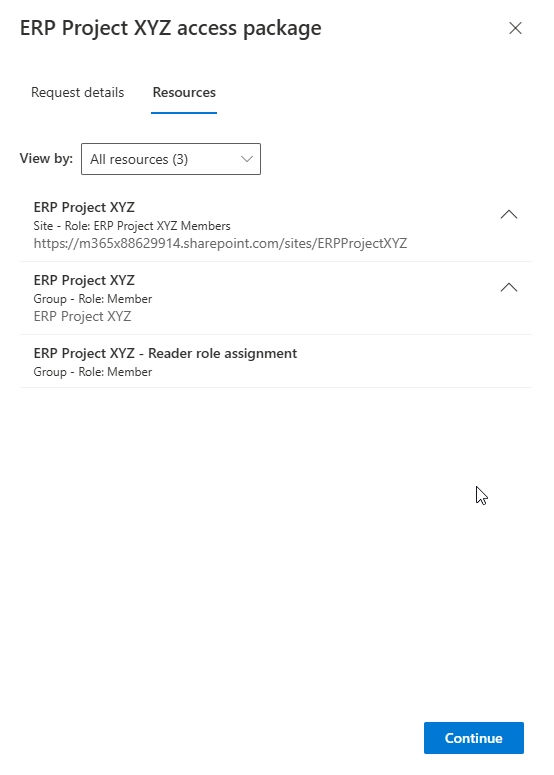
Fulfilling Request Requirements:
The user completes any required fields, such as providing a business justification, before submitting their request.

End-user experience - Approver
Once the request is submitted, the designated approver(s) will receive an email notification and can also manage the request in the My Access portal.

The approver can choose to mange the approval flow directly from the dashboard, or choosing Approvals in the left hand menu.
After opening the request, the approver can choose to Approve or Deny directly, or open the request to see the request details including the provided Business justification


Once approved, the user gains active access to the resources in the package.

End-user experience - External user
The process for external users is slightly different due to additional consent steps, in the midst of it. Here’s how it works:
External users must first sign into the resource tenant. Since they don’t have access yet, they can:
Use a direct link to the access package (provided in the overview as shown in scenario 1), or
Log into the My Access portal with the resource tenant domain:

Once signed in, the user navigates to the Access Packages menu and submits a request, just like an internal user.
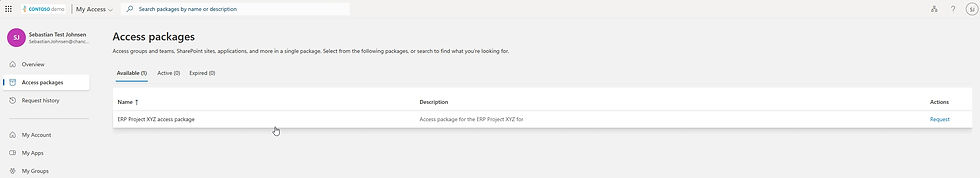
The request process includes providing a short text description of their role for the project, as configured in the Requestor Information section.

Before submitting the request, the user is prompted to consent to sharing data with the resource tenant.

Approver’s Perspective:
The approval process mirrors that of internal users. The only difference is the requestor’s external domain and any specific information configured for external users.

Once approved, the user gains access to the assigned resources.
At their first access to any resource, they’ll be prompted to consent again, creating a guest account in the resource tenant and enabling self-service access.

Streamlined Project Access
This setup ensures seamless access for both internal and external users, with different requirements tailored to their needs. By enabling collaboration across your organization while maintaining strict identity and access governance, you can confidently manage access for diverse user groups.
Scenario 3: Delegating Access Package Administration
Configuration
This task focuses on delegating responsibilities, allowing departments to manage their own access needs. Delegation reduces human errors, minimizes administrative fatigue, and frees up valuable time for IT personnel.
Navigate to the Catalog menu in Entitlement Management under the Identity Governance section of the Entra portal

Creating a Department-Specific Catalog:
Since management has requested a catalog for each department, we’ll create a new catalog for the Design Department.
This ensures resources and Access Packages are grouped logically, making governance easier to manage.

Assigning Roles and Administrators:
Open the newly created catalog and access the Roles and Administrators pane.
Add users or groups to the appropriate roles, giving them the ability to manage their catalog and Access Packages without needing overarching permissions like Identity Governance Administrator.

End-user experience
End users without overarching roles (e.g., Identity Governance Administrator) will only be able to see the catalog(s) for which they have assigned roles. This ensures clarity and prevents accidental or unauthorized access to other catalogs.

Bonus Scenario: Requesting on Behalf of Others
Access Packages aren’t just for managing standard access scenarios—they offer advanced capabilities, too! For instance, the Request on Behalf of feature allows users to request access for others.
A perfect example is requesting Temporary Access Pass (TAP) for other users.
If you’re interested in exploring this functionality, check out Jan Bakker’s post, which dives into configuring TAP requests using this feature.
Conclusion: Access Requested
In this post, we’ve explored the fundamentals of Microsoft Entra Identity Governance Access Packages. We covered how Access Packages streamline identity management through real-world scenarios like automating access for sales teams, enabling collaboration for external users, and delegating administrative tasks. By breaking these use cases into step-by-step configurations, we’ve laid the groundwork for secure and efficient identity governance in your organization.
But this is just the beginning! Access Packages can do so much more. In future posts, I’ll dive into advanced and complex solutions, such as custom extensions, advanced approval flows, and innovative use cases like requesting Temporary Access Passes on behalf of others.
We’ll also explore other exciting areas in identity, endpoint, and access management. Stay tuned for these insights and more.
And now, as always, it’s time for a bad joke to wrap things up:
Why don’t skeletons fight each other?
Because they don’t have the guts! 😎
Before you go, don’t forget to create an account and subscribe to my blog to stay updated on my latest posts. If you found this helpful, be sure to like and share it with your network. See you soon!

well defined
Great information